The third CCSP space, ‘Cloud Platform and Infrastructure Security convey good weightage in the confirmation test. This CCSP space comprehensively clarifies cloud framework segments, hazards related to cloud foundation, various procedures to relieve chances with broad security controls and business coherence, and debacle recuperation intends to protect the cloud information and data. This space serves four significant sub-goals:
1. Appreciating cloud framework parts
2. Examination of dangers related to a cloud framework
3. Planning and arranging proficient security controls
4. Anticipating compelling fiasco recuperation and business coherence the executives
Grasping cloud foundation segments
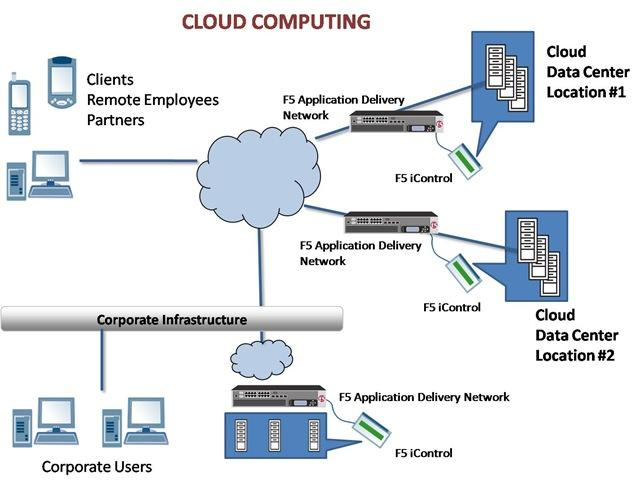
This first sub-objective anticipates that the certification seeker should comprehend the foundation segments of the cloud including the actual climate, network correspondence, computational assets, virtualization, stockpiling, and the executive's plans.

The actual climate comprises server farms that catch and store the clients’ and hierarchical information. These server farms compulsorily need to fall flat verification that can be accomplished somewhat by having different back-ups and power units. Virtualization empowers clients to get their information put away in the cloud with no extra equipment while improving productivity. The CCSP assessment taker is relied upon to know all such ideas of cloud foundation and segments.
Examination of dangers related with cloud foundation
In the wake of having perceived the cloud foundation parts, the competitor has to realize how to investigate hazards related to cloud framework security. This sub-objective rotates around hazard appraisal and investigation, cloud assault vectors, virtualization dangers, and countermeasure methodologies like access controls. The up-and-comer is required to comprehend the danger appraisal cycles like outlining, evaluating, checking, and reacting to the dangers. What’s more, the competitor should be acquainted with the ideas of subjective and quantitative danger evaluation.
Planning and arranging effective security controls
When the dangers are surveyed, suitable security controls need to execute, following which the under-referenced basics are relied upon to be known:
· Physical and Environmental Protection (for example on-premise)
· Framework and Communication Protection
· Virtualization Systems Protection
· The board of Identification, Authentication, and Authorization in Cloud Infrastructure
· Review Mechanisms
Utilizing sufficient security controls is a proficient method to alleviate hazards. This can be accomplished by guaranteeing that all actual resources are found safely. All passage and leave focuses should be observed and workers should be given identifications in the wake of performing different individual verifications.
While inspecting is done in various business conditions, cloud evaluating is essential however isn’t difficult to direct as the information may be put away in various areas in the cloud and cloud suppliers may be reluctant to share the data.
In such a manner, the CCSP test approves the competitor’s ability about cloud review objectives and various sorts of review reports (SOC1, SOC2, SOC3).
Making arrangements for viable debacle recuperation and business progression the executives
In the wake of utilizing sufficient security controls, debacle recuperation and business progression in the cloud should be accomplished. These themes structure the central goal of any data security conversation and program.

The competitor should have a flawless comprehension of the BC and DR in the cloud climate and should secure exhaustive information about how to re-draw it. The BIA or ‘Business sway investigation’s strength must be administered once the client’s information is moved to the cloud.
The confirmation searchers should procure a top to bottom comprehension of the cloud climate, business necessities, and security changes in the cloud. As per this, competitors should achieve the capacity to comprehend the DR and BC methodologies, plan and carry out something very similar. Get more insight concerning free versatile security applications, Geekeno is consistently there to assist you with excursion your inquiries! Kindly don’t hesitate to interface with us at info@geekeno.com and contact us at +919599710432.